Security Testing Overview
Security testing is a sort of software testing that identifies vulnerabilities, hazards, and dangers in a software program and guards against intruder assaults.
Implementing Shift Left Security
DevSecOps is a form of DevOps that incorporates security into the SDLC—security tools and processes are part of the pipeline from the beginning. This approach improves application security before releases reach production. It eliminates the silos dividing security and DevOps teams.
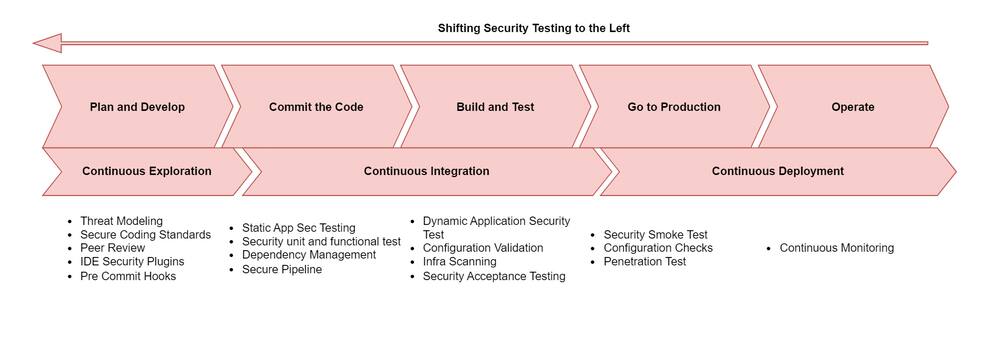
To implement DevSecOps of shifting left security testing:
Incorporate security tools into the CI/CD pipeline at the left of the process: Threat Modelling, Scanning vulnerabilities, Secrets, SAST, SCA, and declarative configuration.
Ensure collaboration between security and DevOps teams.
Review all infrastructure security policies before deployment.
Implement runtime security controls to protect production environments.
Build observability into applications to enable effective security monitoring.
Create an incident response process to ensure an effective response to security incidents.
Penetration Testing
Few weeks prior to Go-live: Penetration test is conducted in the pre-prod environment (ideally in the most prod like environment)
Key Stakeholders involved in decision making: Security Architect, Delivery Team, Risk Assessor, Internal Audit, Digital AVPs
Frequency: Depending on the budget and criticality of the project – one or more than one pen test maybe conducted
Frequency: Annually
Monitoring and Ensuring Observability
DevOps security requires consistent visibility using:
Monitoring tools - allow teams to track the system state using various metrics.
Observability tools - allow teams to debug systems by exploring undefined patterns and properties.
DevOps teams must regularly report on system performance and health from the customer’s perspective. Monitoring should focus on defined metrics and objectives, while observability investigates unknowns. Teams should have access to tooling to track and analyze production infrastructure issues.
Tools
Withing the organization Veracode is widely used tool for Security.








