| Control ID |
Control Description |
Coverage in CI |
|---|
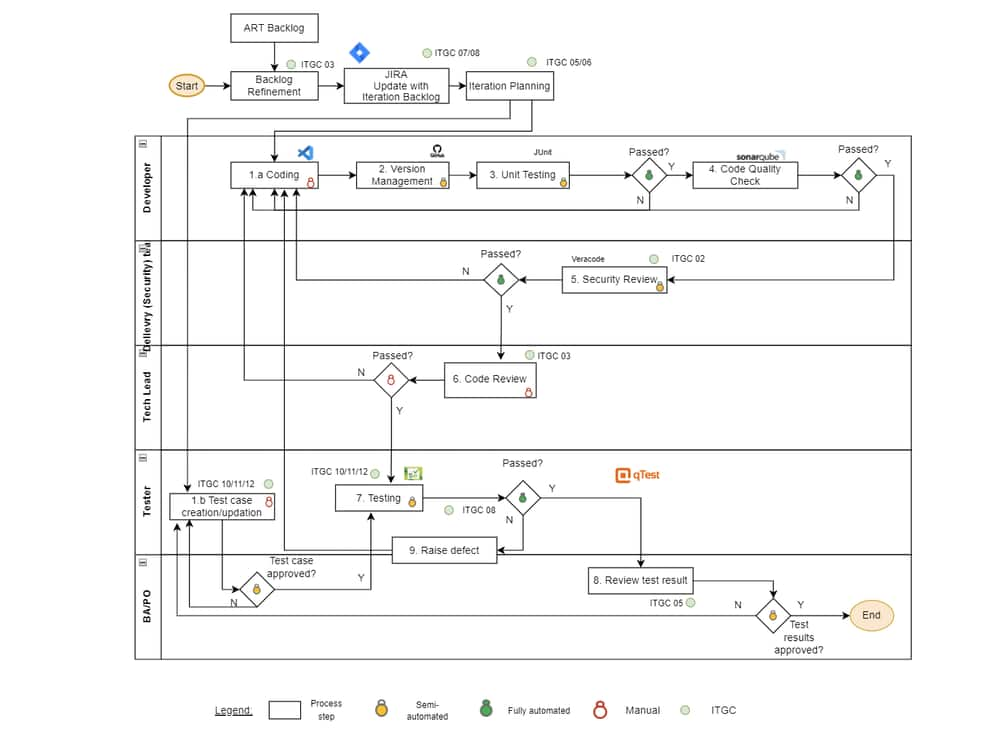
ITGC02.Information Security Policies and Standards Compliance Management
|
The enterprise has processes to monitor compliance with Information Security policies and standards.
Note: Overall security review with involvement of IT Security team before a release.
Control activities:
Non-compliance to Information Security policies and standards is monitored, tracked and are reported on
Non-compliance to Information Security policies and standards are actioned by the business and/or IT owner(s) based on risk and impact to the organization
|
Highlighted action is covered in Continuous Integration
|
ITGC03.Development Methodology
|
The organization has a solution development methodology that contains a set of requirements, which includes security and processing integrity controls, that are adhered to throughout the solution development lifecycle.
The solution development methodology is documented/updated and reviewed/signed-off by the IT owner(s) on a periodic basis
The solution development methodology requires that any changes identified will be authorized and prioritized by business owners and aligned to quarterly objectives and desired business outcomes
The solution development methodology requires planning for the ongoing maintenance of the systems/solutions developed
The solution development methodology requires defining new and changed IT services and service levels of developed systems/solutions
The solution development methodology requires initiative closure and acceptance be performed by the business owner for work having a defined start and end date. For work delivered through agile continuous delivery, the business owner accepts all changes and authorizes them at production release.
|
Highlighted actions are covered in Continuous Integration
Last 3 actions are covered in Continuous Deployment
|
ITGC05.User Involvement
|
The enterprise has a solution development methodology that defines and maintains business functional and technical requirements that are endorsed by all stakeholders.
Control activities:
Product/business owner(s) review and authorize/approve all work/requirements as part of quarterly planning
Product/business owner(s) review and authorize/approve the final choice of solution, acquisition approach and high-level design, aligned to the desired business outcome. This is achieved through the quarterly planning process
Product/business owner(s) review and authorize/approve User Acceptance Testing (UAT) results
|
Highlighted action is covered in Continuous Integration
First 3rd action is covered in Continuous Deployment
|
ITGC06.Compliance with Development Methodology
|
The organization has a solution development methodology that contains a set of requirements, which includes security and processing integrity controls, that are adhered to throughout the system development lifecycle.
Control activities:
In-house IT developments (including infrastructure) and/or procured systems comply with the solution development methodology
|
Highlighted actions are covered in Continuous Integration
|
ITGC07.Change Management
|
Requests for program changes and system changes (including maintenance) are standardized, logged, evaluated, prioritized and approved. The enterprise maintains a change management repository to track all requested changes, including the status of approved, in-progress and closed changes. IT Management implements system software that does not jeopardize the security of programs or the integrity of data stored on the system. Post-implementation reviews are conducted to confirm outcomes and results.
Control activities:
All change requests are documented/logged in a change management repository which includes the description of change. The implementation plan and a backout plan are required for teams with system limitations and not able to follow risk-based automated deployments as documented in the solution development methodology.
All changes are authorized by the business and/or IT owner(s) or designates(s) and medium/high risk changes are reviewed in the weekly Change/Technical Advisory Boards (CAB /TAB)
All changes are tested in a non-production environment prior to production implementation. In cases where testing in a non-production environment is not possible, this is documented within the RFC
Post-implementation validation is conducted and validation results are reviewed
|
Highlighted actions are covered in Continuous Integration
Fifth action will be covered in Continuous Deployment
|
| ITGC08.Emergency Change Management |
Emergency change requests are documented and subject to formal change management procedures. A post-implementation review is conducted to confirm outcomes and results.
Control activities:
All emergency change requests are documented/logged in a change management repository which includes the description of the emergency change
Emergency changes are authorized by the business and/or IT owner(s) or designates(s). Authorization is automated for teams following risk-based automated deployments.
Post-implementation validation for emergency changes validation results are reviewed
|
Highlighted actions are covered in Continuous Integration
Fifth action will be covered in Continuous Deployment
|
| ITGC10.Testing |
A test strategy must be followed which includes testing scope, goals, approach, tools, roles, environments, test exit criteria and timing of test activities. It takes into consideration testing requirements including security, architectural design, internal controls and privacy.
Control activities:
Testing artificats are prepared which include test design, test cases/steps, test coverage, test issues, expected and actual results.
Testing is executed in accordance with the test
strategy, testing artifacts are retained and testing results are reviewed and authorized/approved by the business and IT owners(s) prior to production implemention
|
Highlighted actions are covered in Continuous Integration
|
| ITGC11.System Interfaces |
A test strategy must be followed which includes systems interface testing and is established to ensure data transmissions are complete, accurate and valid. It takes into consideration environments, security, internal controls and privacy.
Control activities:
Systems interface testing artificats are prepared which include test design, test cases/steps, test coverage, test issues, expected and actual results
Systems interface testing is conducted in non-production environments (source and destination), testing artifacts are retained and test results are reviewed and authorized/approved by the business and IT owner(s) prior to production implementation
|
Highlighted actions are covered in Continuous Integration
|
| ITGC12.Data Conversion and Migration |
A test strategy must be followed which includes includes system and data conversion/migration testing and is established to ensure data coversion/migration is complete, accurate and valid. It compares original and converted data including audit trails and a recovery plan if conversion/migration fails and takes into consideration security, internal controls and privacy.
Control activities:
Data conversion/migration testing artifacts are prepared which include test design, test cases/steps, test coverage, test issues, expected and actual results.
Data conversion/migration testing which includes comparing original and converted/migrated data (e.g. record counts, validation of financial integrity, etc.) is conducted, testing artifacts are retained and test results are reviewed and authorized/approved by the business owner(s) prior to production data conversion/migration
|
Highlighted actions are covered in Continuous Integration
|