Introduction
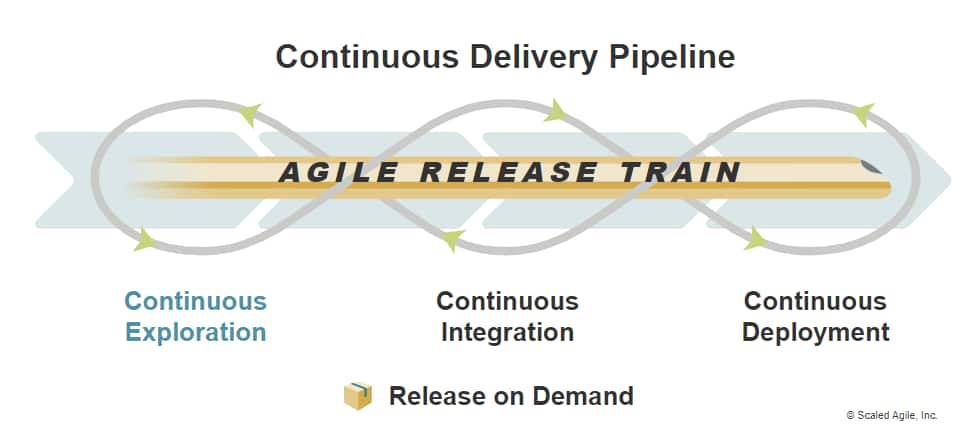
Continuous Exploration (CE) is an aspect of the Continuous Delivery Pipeline that drives innovation and fosters alignment on what should be built by continually exploring the market and customer needs, defining a vision, roadmap, and set of epics for a solution.
Continuous Exploration (CE) is the first aspect of the four-part Continuous Delivery Pipeline (CDP), which also includes Continuous Integration (CI), Continuous Deployment, and Release on Demand.
| Control ID | Control Description | Coverage in CE |
|---|---|---|
ITGC01.Information Security Policies and Standards |
An Information Security Management System (ISMS) plan and policy exists and has been approved by Executive Management. Control activities:
|
|
| ITGC04.Application Controls | The solution development methodology through architectural and security practices includes requirements that information systems are designed with to include application controls that support complete, accurate, authorized and valid transaction processing. Control activities:
|
|
| ITGC06.Compliance with Development Methodology | The organization has a solution development methodology that contains a set of requirements, which includes security and processing integrity controls, that are adhered to throughout the system development lifecycle. Control activities:
|
|
| ITGC05.User Involvement | The enterprise has a solution development methodology that defines and maintains business functional and technical requirements that are endorsed by all stakeholders. Control activities:
|
|
| ITGC09.Promotion to Production | A process is established to restrict access to authorized individuals functions only for the migration of accepted solutions/software releases into production.
|
|
| ITGC10.Testing Strategy | A test strategy must be followed which includes testing scope, goals, approach, tools, roles, environments, test exit criteria and timing of test activities. It takes into consideration testing requirements including security, architectural design, internal controls and privacy. Control activities:
|
|
| ITGC11.System Interfaces | A test strategy must be followed which includes systems interface testing and is established to ensure data transmissions are complete, accurate and valid. It takes into consideration environments, security, internal controls and privacy. Control activities:
|
|
| ITGC12.Data Conversion and Migration | Control activities:
|
|
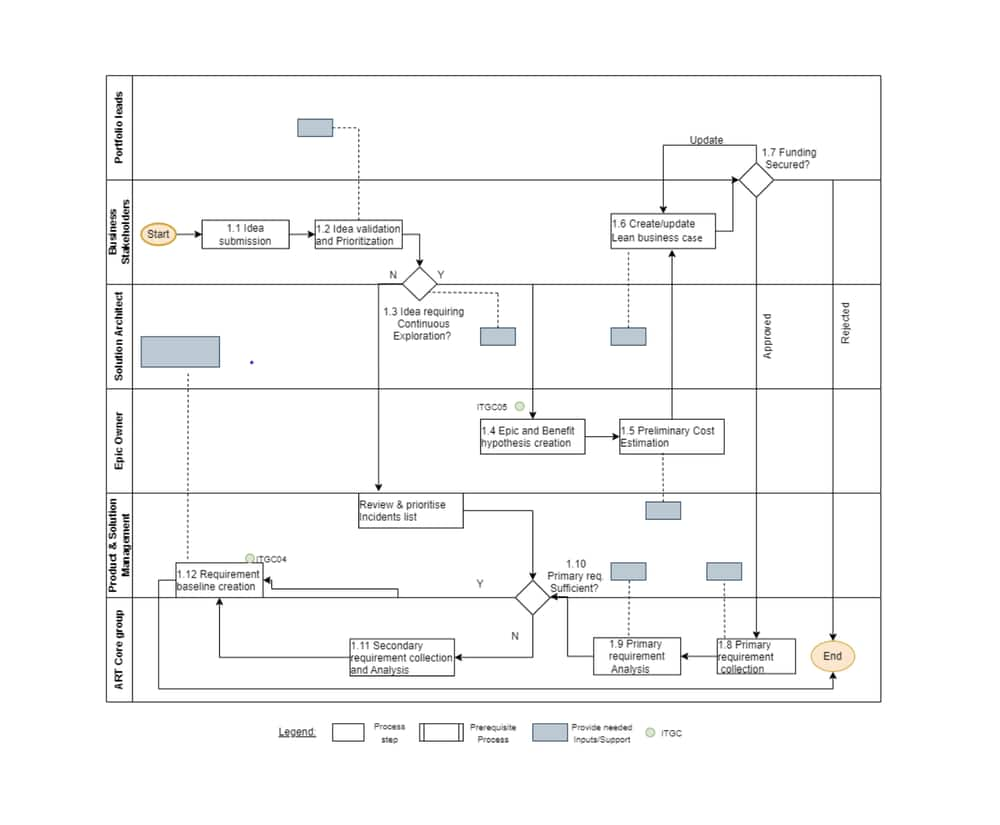
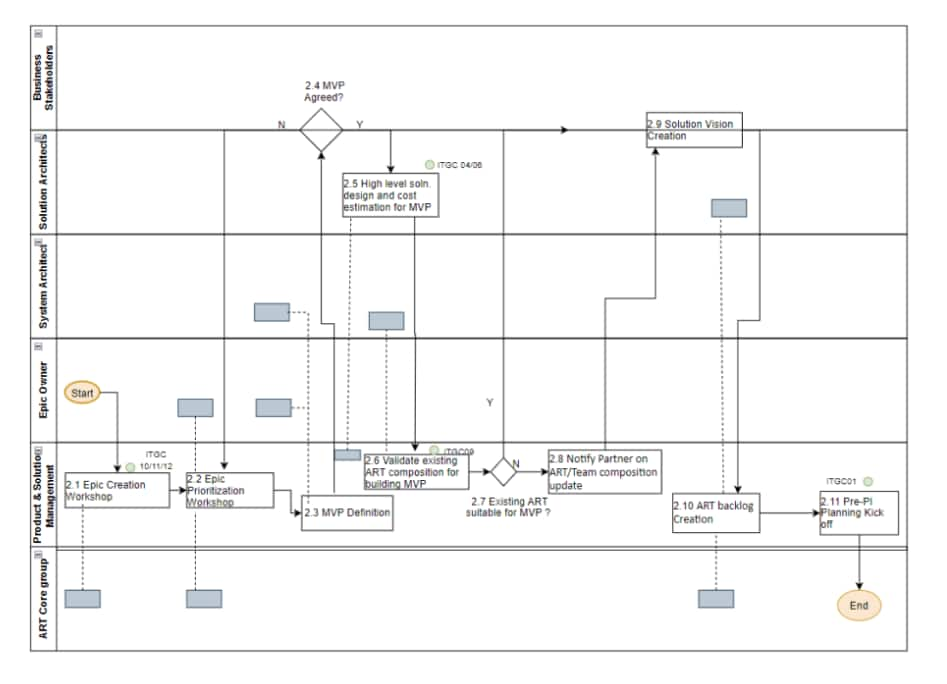
Artifacts relevant for Continuous Exploration
Epic Backlog
Solution design & architecture
Defined MVP
Cost estimation report
Solution vision & roadmap
Program/ART Backlog




