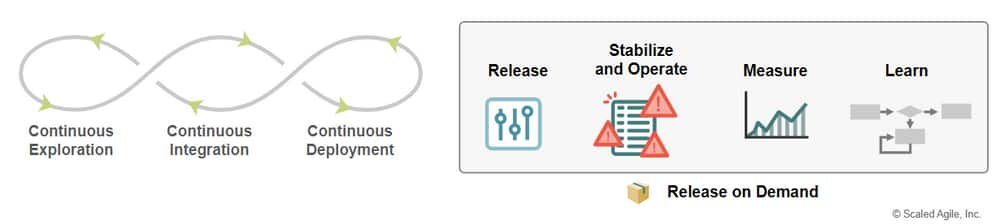
Overview
Release on Demand is an aspect of the Continuous Delivery Pipeline that releases new functionality immediately or incrementally based on business and customer needs.
The Agile Product Delivery describes how the ‘develop on cadence; release on demand’ dimension creates the ability to deliver valuable solutions to end users with optimal timing and frequency.
Three Questions for Product and Solution Management
When Should a Release Happen?
What elements of the solution should be released?
Which end-users should receive the release?
The Four Activities of Release on Demand
Release
- the practices needed to deliver the solution to end users.
Stabilize and Operate
- ensures the solution is working well.
Measure
- how to quantify if the newly-released functionality.
Learn
- collecting feedback and preparing for the next loop.
| Control ID | Control Description | Coverage in RoD | |
|---|---|---|---|
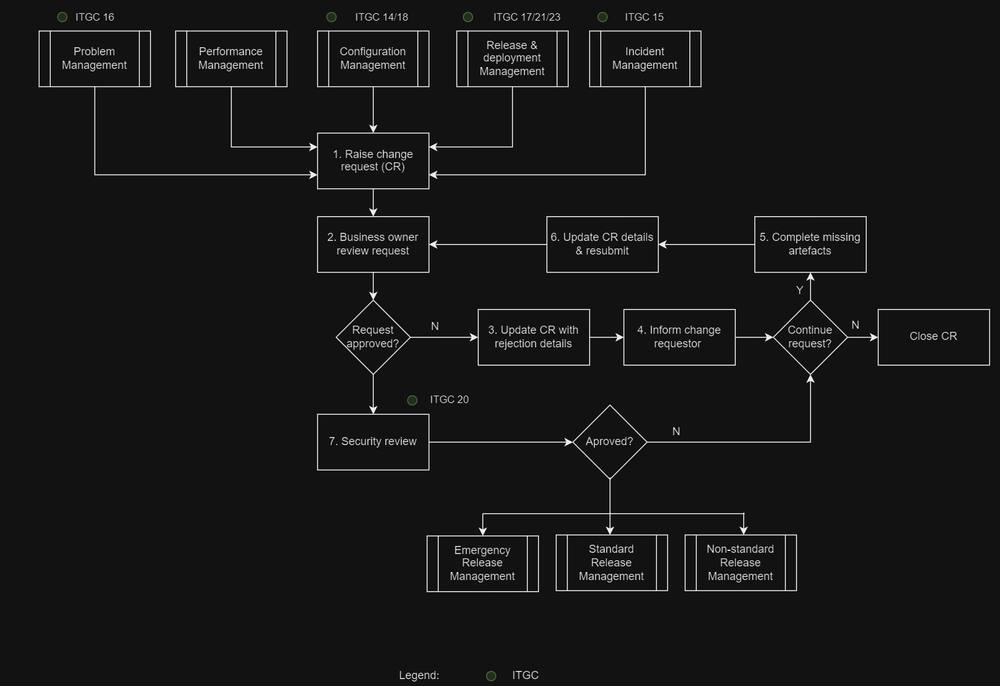
ITGC07.Change Management |
Requests for program changes and system changes (including maintenance) are standardized, logged, evaluated, prioritized and approved. The enterprise maintains a change management repository to track all requested changes, including the status of approved, in-progress and closed changes. IT Management implements system software that does not jeopardize the security of programs or the integrity of data stored on the system. Post-implementation reviews are conducted to confirm outcomes and results. Control activities:
|
|
|
ITGC08.Emergency Change Management |
Emergency change requests are documented and subject to formal change management procedures. A post-implementation review is conducted to confirm outcomes and results. Control activities:
|
|
|
ITGC09.Promotion to Production |
A process is established to restrict access to authorized individuals functions only for the migration of accepted solutions/software releases into production.
|
|
|
ITGC13.Configuration Management and Monitoring of Configuration Change |
A process is established for implementing and maintaining security configurations, and for monitoring security configuration changes. Control activities:
|
|
|
ITGC14.Job Scheduling and Monitoring |
IT Management has documented and established IT operational procedures, including job scheduling changes/events and incident management processes, to ensure the integrity of batch processing. Control activities:
|
|
|
ITGC15.Incident Management |
IT Management has defined and implemented an incident management system such that operational issues, data integrity issues and security-related issues are recorded, analyzed, resolved in a timely manner and reported to Management. Control activities:
|
|
|
ITGC16.Problem Management |
IT Management has defined and implemented a problem management system such that operational issues, data integrity issues and security-related issues are recorded, analyzed, resolved in a timely manner and reported to Management. Control activities:
Note: Problems identified through incidents, have corresponding incident tickets referenced
|
|
|
ITGC17.Backup Monitoring |
IT Management has implemented a strategy for cyclical backup of data and programs. Control activities
|
|
|
ITGC18.Backup Media Testing |
The restoration of information is periodically tested. Control activities:
|
|
|
ITGC20.Security Event Monitoring |
IT Security monitors and logs security activity at the network, platform/server, and database levels and identified security violations are reported to Management. Control activities:
|
|
|
ITGC21.User Access Provisioning/23.Segregation of Duties |
Procedures exist and are followed relating to timely action for requesting, granting, suspending and closing user accounts. Controls relating to appropriate segregation of duties (SoD) over requesting and granting access to systems and data exist and are followed. Control activities:
|
|
|
ITGC24.Threat and Vulnerability Management |
Appropriate controls, including firewalls, intrusion prevention/detection systems and vulnerability assessments, exist and are used to prevent and detect unauthorized access to information assets. Control activities:
|
||
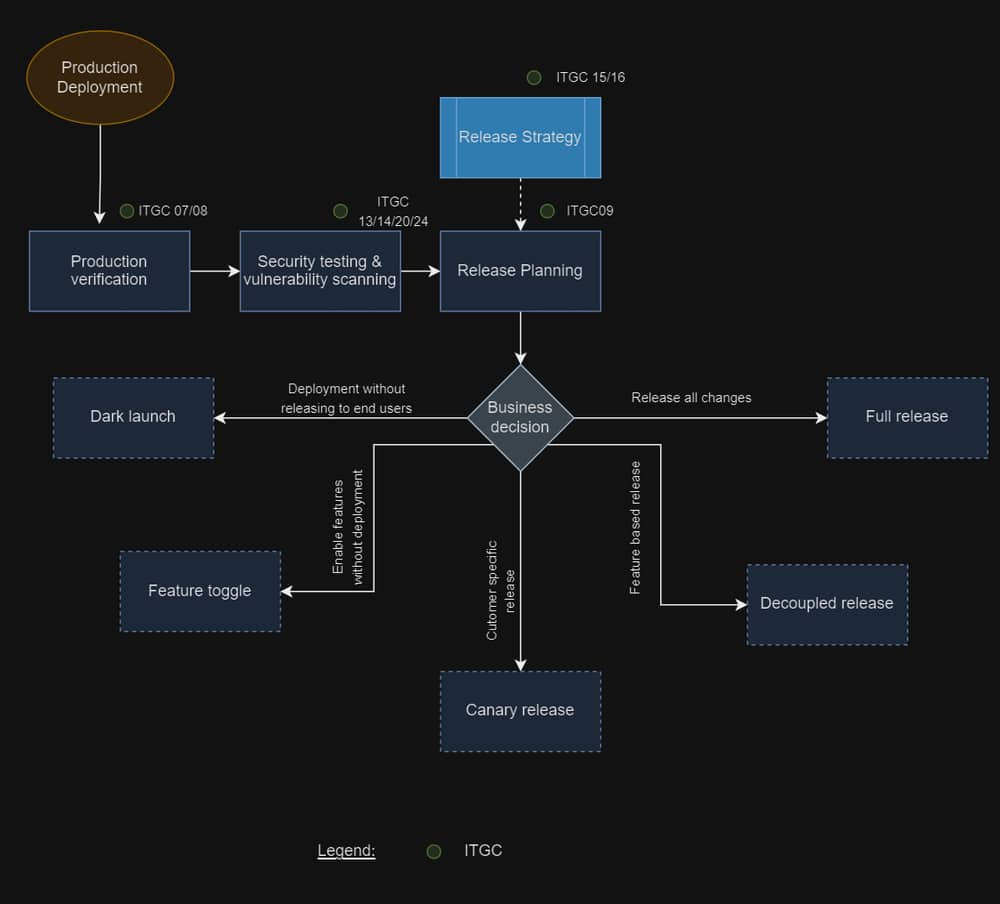
Release & Deployment process
This process document covers three variations of release, basis the nature of demand and scenario release requests can be classified as below.
Emergency Release
- P1 or P2 incidents which initiate P1 or P2 Change can be considered for Emergency Release Management process. Delivery Lead will provide approval to qualify Emergency Release scenarios based on inputs from Business, Security, Testing and/or any dependent party. Delivery Lead approval is mandatory to trigger Emergency Release process.
Standard Release
- Standard release are changes to a service or to any of the operational assets of the network where the implementation process and the risks are known upfront. In some cases, some standard changes are subject to established policies and procedures, they are the easiest to prioritise and implement, and often don’t require approval from a risk management perspective.
Non-Standard Release
- Non-Standard release are those that must go through the entire change process before being approved and implemented. If they are determined to be high-risk, a change approval board must decide whether they will be implemented.




